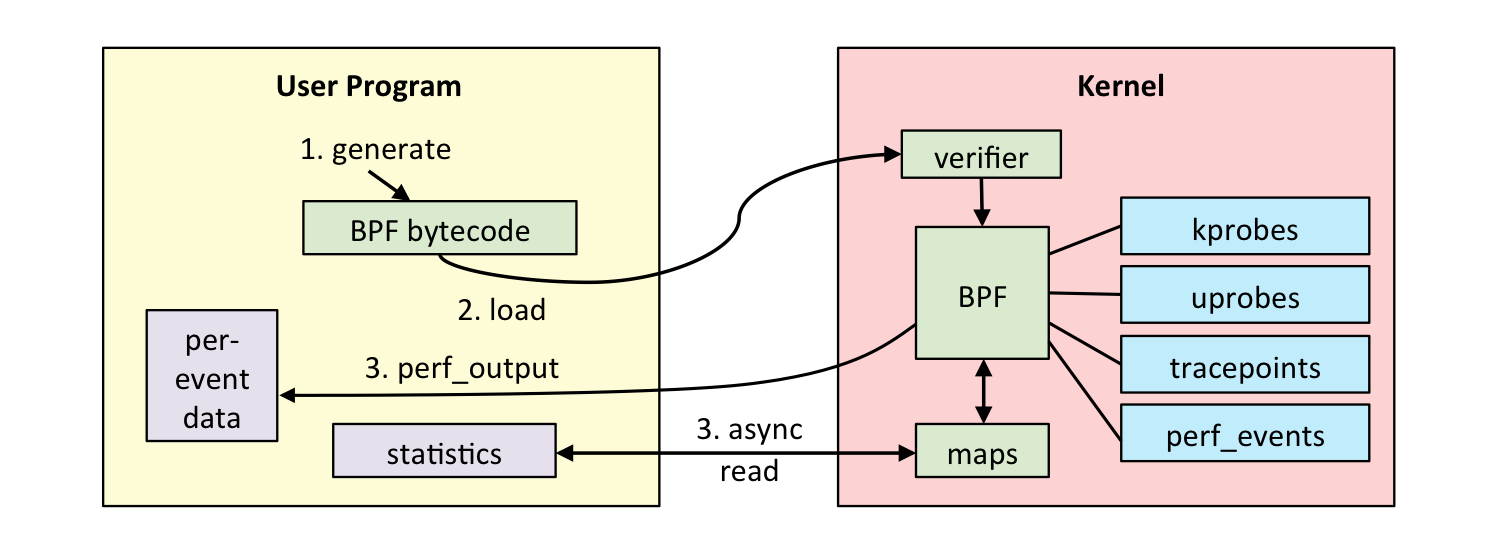
BPF
bpf
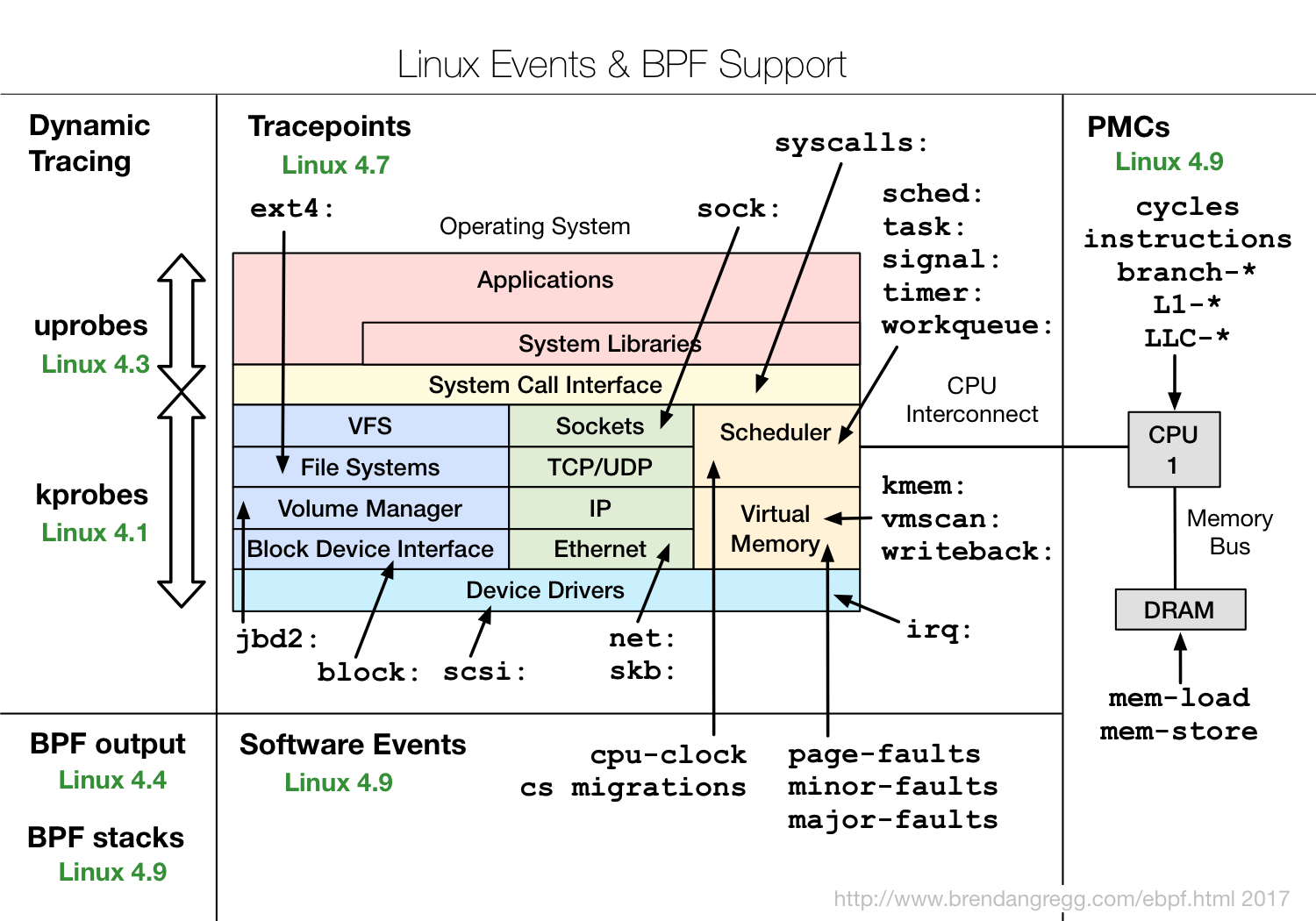
image from http://www.brendangregg.com/ebpf.html
- kprobes
- kprobes can trace arbitrary functions, but may easily break from one Linux version to the next
- tracepoints
- tracepoints are more stable, they remain mostly the same
- and documented in
/sys/kernel/debug/tracing - can list with
sudo perf list
- perf
- http://www.brendangregg.com/perf.html
refer:
https://stackoverflow.com/questions/45618274/are-tracepoints-redundant-in-linux-kernel-after-kprobes-support-for-ftrace
Projects/Tools/Examples
- bcc
- bpftrace
- libbpf
- libbpf-tools
- bpftool
- sampes/bpf/ in kernel tree
- perf, ftrace
Usage
- cgroup
- systemd service
- tc-bpf
- iptables bpf
- socket bpf
- ip-route bpf
- sockmap
Build kernel samples
# kernel config
gunzip -c /proc/config.gz > .config
make oldconfig && make prepare
# install headers
make headers_install -j8
# build bpf
make M=samples/bpf -j8
# run
ulimit -l unlimited
sudo ./sockex1
Must Read
bpf.hin kernel treesudo bpftool feature probeoutput- Linux Socket Filtering aka Berkeley Packet Filter (BPF)
-
Notes on bpf series
-
Run a BPF program on socket lookup
- presentation
- inet_lookup
- BPF_PROG_TYPE_SK_LOOKUP
-
SOCKMAP - TCP splicing of the future
- two bpf prog attached to one sockmap
- BPF_MAP_TYPE_SOCKMAP
- BPF_SK_SKB_STREAM_PARSER, BPF_SK_SKB_STREAM_VERDICT
TYPE(not complete)
- socket: for iptables –bpf, setsockopt
- BPF_PROG_TYPE_SOCKET_FILTER
- cgroup/sock:
- BPF_PROG_TYPE_CGROUP_SOCK
- BPF_CGROUP_INET_SOCK_CREATE
- parameters: see
bpf_ctx_convertin vmlinux.h- bpf_sock or __sk_buff
- cgroup_skb/egress: for systemd cgroup
- BPF_PROG_TYPE_CGROUP_SKB
- BPF_CGROUP_INET_EGRESS
- see
bpf_sec_definlibbpf.c - see samples in
linux/samples/bpf/
